Most Azure programs don't fail in compute or storage. They get stuck at the edge.
You reach a point where the same question comes back in every security review, every incident postmortem, and every compliance workshop:
Do we stay Azure-native and ride Microsoft's global backbone, or do we decouple the edge and make the origin effectively invisible?
This is not a "tooling preference" decision. It is an operating model decision. It determines how you handle audits, how you troubleshoot, how you design DNS, and how much time your team spends on WAF tuning versus shipping work.
Below are three patterns I see repeatedly in enterprise and regulated environments. I'm not ranking them. I'm showing where each one wins and where each one bites.
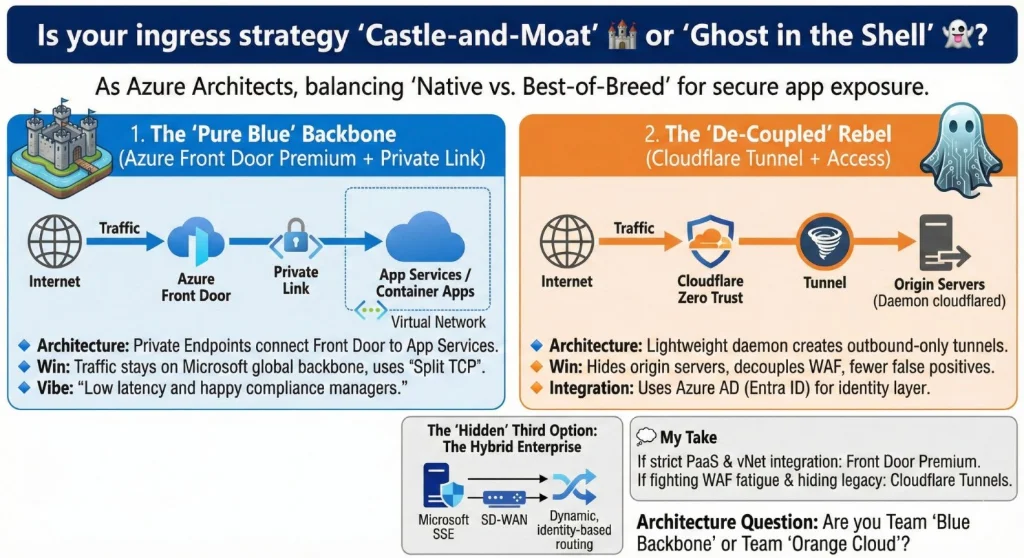
Pattern 1: Azure Front Door Premium + Private Link
Principle: Microsoft Edge, private origin, Azure-governed controls.
What this architecture looks like
- Azure Front Door Premium provides global ingress, TLS termination, routing, and WAF at the edge.
- Your origin stays private using Private Link patterns
Why teams choose it
- Audit posture is clean: Private origins and a single-cloud control plane simplify conversations with risk and compliance.
- Strong performance by default: Global routing and edge termination usually improves user experience without complex tuning.
- Native platform governance: RBAC, policy, diagnostics, and operational consistency across Azure.
Where it breaks in real life
- DNS is not a detail. Private DNS zones, name resolution, and split-horizon behavior must be designed early.
- Troubleshooting can become slow if you do not instrument edge logs, WAF logs, origin logs, and private network telemetry end-to-end.
- Origin constraints and support boundaries matter. Validate protocol, port, and origin-type limitations before you commit.
Best fit
- You are PaaS-first or moving there.
- You want a Microsoft-governed model with predictable audits.
- You prefer fewer vendors and fewer operational surfaces.
Executive summary: This is the strongest default when you want private origins with a clean Azure governance story and your platform foundations are mature.
Pattern 2: Cloudflare Tunnel + Access
Principle: No inbound exposure. Publish without opening doors.
What this architecture looks like
- You do not open inbound ports to the internet.
- A connector (cloudflared) runs inside your network and establishes outbound-only tunnels to Cloudflare.
- Cloudflare sits at the edge, enforces access policy (often integrated with Microsoft Entra ID), and forwards traffic over the tunnel to the private origin.
Why teams choose it
- Origins become hard to discover and hard to scan. No public IP. No public listener.
- Legacy-friendly publishing. Works well for non-standard apps and awkward backend patterns.
- Operational relief from "WAF fatigue." Many teams move here when WAF false positives and exception churn become permanent work.
Where it breaks in real life
- Cloudflare becomes a hard dependency for ingress. You need an explicit stance on resilience, change control, and vendor risk.
- Connector lifecycle is real work. Versioning, rollout, monitoring, and capacity planning must be treated as production operations.
- Visibility can split across Azure + Cloudflare. Your incident response runbook must cover both.
Best fit
- You have legacy apps or non-standard origins.
- You want publish-without-exposure as a security baseline.
- You accept Cloudflare as a strategic ingress layer.
Executive summary: This is the cleanest way to reduce exposed surface area quickly, especially when modernization timelines are long.
Pattern 3: Microsoft SSE (Global Secure Access) + SD-WAN
Principle: Identity-based access for workforce and internal apps, not "public ingress."
What changes
- You move away from static IP allowlists and VPN sprawl.
- Access becomes policy-driven and identity-centered.
- Often paired with SD-WAN to steer traffic automatically from branches and remote sites.
Best fit
- Internal apps, workforce access, branch connectivity.
- Programs actively reducing VPN complexity.
Executive summary: If your biggest pain is user-to-app access, SSE is often a more strategic conversation than edge WAF selection.
The Decision Framework
(Use this in a steering committee)
Most debates get stuck on "which WAF is better." That is the wrong question.
Ask these five instead:
- Are we protecting public APIs, internal apps, or both?
- Do we need private origins or invisible origins?
- What is our tolerance for vendor dependency at the edge?
- Are we ready to run DNS and private connectivity like a product, not a project task?
- How will incident response work end-to-end across edge, identity, and origin?
If you cannot answer these, you are not choosing an architecture yet. You are choosing future rework.
Case Study: Regulated Environment with "WAF Fatigue"
(Anonymized)
Context
- Financial services team with a mixed estate: App Service, AKS, and legacy IIS apps.
- Frequent audits and strict security controls.
- Operational pain: WAF tuning took weeks per cycle. False positives and exception churn eroded confidence.
What worked
- Azure Front Door Premium + Private Link for Azure-native PaaS workloads
- Cloudflare Tunnel + Access for legacy and awkward origins
The rule that kept it scalable: If a workload cannot meet the private-origin standard quickly, it must meet the invisible-origin standard.
Outcome
- Reduced exception churn
- More predictable audit discussions
- A clearer split of responsibility between platform and application teams
My Take
- If you are PaaS-heavy and want private origins with an Azure-governed model, Front Door Premium + Private Link is the strongest default.
- If you must hide origins, publish legacy safely, or are battling WAF fatigue, Cloudflare Tunnel is hard to beat.
- If your focus is workforce access and reducing VPN sprawl, Microsoft SSE + SD-WAN is the strategic pivot.
Question for Architects and Platform Leads
What edge pattern are you running today, and what made you choose it? I'd love to hear what worked, what didn't, and what you'd change if you could start over.